Simple fix for Mac OS X 10.6.3 Samba Write Access problem
Upgrading to Mac OS X Snow Leopard 10.6.3 was a painless procedure until I tried to access some SMB mounts… suddenly I had no write access to my samba drives! I was presented with this error message:
The operation can’t be completed because you don’t have permission to access some of the items.
Thankfully there’s a workaround of sorts and it is pretty straightforward.
Fixing the Samba/SMB write access problem in 10.6.3:
* Open smb.conf on the samba server in your favorite text editor
sudo nano /etc/smb.conf
* Find the global samba settings section under [global] and add the following line:
unix extensions = no
* Save and close smb.conf (in nano, Control-O followed by the return key to save, then Control-X to exit)
* Restart the smb server
The cause of the SMB error in Mac OS X 10.6.3:
After digging around I found the cause on SplatDot, and I can confirm I had the same error messages pertaining to wide links and unix extensions enabled at the same time, two parameters which are incompatible. This is why the fix works, you are disabling unix extensions (of course, you could disable wide links but there is a performance hit to that method) and the error will no longer occur.
I imagine this is just a bug in the way that Mac OS X 10.6.3 handles SMB shares and it will probably be fixed relatively quickly by Apple, and when it is fixed you can and should reactivate unix extensions again on the Samba server. Doing so is just a matter of removing the unix extensions = no line from the smb.conf file.
Grep Tricks for Linux Users
The first of these tricks allows you to create a list of files that contain whatever string you are looking for. It uses the -l (list just the file names, not the matched content) option plus the -r option for recursing through subdirectories. This can help you find files that you might be looking for without distracting you with all the reasons particular files matched your search criteria.
grep -rl "string you want to find" *
Example:
$ grep -rl "meeting minutes" * ARK2010/02-02-notes ARK2010/TBD Jan2010/TASkForce2 Mar2010/TaskForce2
Another useful trick with grep on Linux allows you to specify a Perl regular expression in your search term. In this example, we can give grep an expression that allows it to match on mulitple strings, much like egrep. You can get far more complicated than the examples shown, but here’s the basic syntax:
grep -P "while|for" * grep -P 'photo\.gif' *
You can also combine grep with find commands to get some useful extractions of text from target files.
find . -name "*.r" -exec grep "rho" '{}' \; -print
Of course, one of the most useful grep tricks that I’ve come across so far is the one that provides some context along with your find. Instead of only displaying the lines containing the specific text you were searching for, you can print lines appearing before and after the matched lines -- often required to determine whether tha "match" is really what you’re looking for.
You can specify how many lines you want to see before your matched string with the "B" (for "before") option and the number of lines following the match with the "A" (for "after") option.
$ grep -B 2 -A 2 echo *
--
while1-while [ $n -lt 5 ]
while1-do
while1: echo hello
while1- ((n +=1))
while1-done
--
whoison-#!/bin/bash
whoison-
whoison:echo hello, $USER
whoison:echo Look who is logged in!
whoison:echo ===========================
whoison-who | awk '{print $1}' | sort | uniq
whoison:echo ===========================
Notice that more than five lines were displayed in the second block of lines above because "echo" appeared more than once in these lines.
How to block a website from Safari, Firefox, or Chrome
Do you want to keep yourself or your employees from wasting time on certain websites? Maybe you don’t want your child to see some of the virtual trashbins of the internet? By editing the /etc/hosts systems file, you can block any website, and here’s how to do it.
Easily block websites from being accessed in Safari, Firefox, or the Chrome browser
* Launch the Terminal and type the following command, you will need to enter a root password:
sudo pico /etc/hosts
* Using your arrow keys navigate down and create a new line in the file
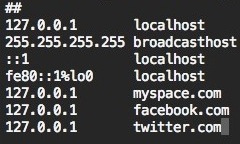
* You can block any website by following the format of:
127.0.0.1 facebook.com
127.0.0.1 myspace.com
127.0.0.1 twitter.com
* Exit and save /etc/hosts by hitting Control+O and then the Return key
Next you will need to flush your DNS cache for the changes to take effect, this is done through the Terminal as well with the following command in 10.6:
sudo dscacheutil -flushcache
Unblocking the sites is simply a matter of removing them from the /etc/hosts file and flushing your DNS cache again. This whole thing works by pointing the domains you want blocked to your machines localhost (127.0.0.1). If you wanted to be tricky you could point the blocked domain to a different IP address entirely, like 74.125.19.103 (Google.com in English). For this purpose, you can get any websites IP address by typing nslookup domain.com into the Terminal.
If you want a network wide solution to blocking websites or any other network services, you’d need to modify your routers settings.
Prevent Google Chrome’s updater from running
An earlier hint I found said to use Lingon to edit the launchd file and remove Google’s updater task from the Chrome browser. It works great until the next time you run Chrome.
To foil Google/Chrome once and for all, use Lingon to disable the launchd task, and then go to your user’s Library/Google folder and delete the contents of GoogleSoftwareUpdate. Not done yet -- now you must use Terminal to prevent the next launch of Chrome from re-establishing the task.
In a Terminal window, cd ~/Library/Google and type chmod 111 GoogleSoftwareUpdate. Now the whole folder is write locked, and Chrome can’t reload the software update contents, and it won’t recreate the launchd task either.
Block and manage IP blacklists easily with PeerGuardian for Mac OS X
PeerGuardian is a free open source tool that allows you to easily block large numbers of IP addresses in Mac OS X. It automatically maintains an internal IP blacklist to block IP’s deemed unsafe or dubious in nature, and also allows for multiple IP lists with the ability to block entire protocols. Other features include logging and maintenance tools to see what exactly is being blocked. Many people use PeerGuardian in conjunction with an extensive external IP blacklist when using P2P file sharing applications and networks to better maintain their security and privacy.
Many Mac users are surprised to note that Apple.com is a blocked IP in the PeerGuardian IP list, but HTTP and FTP traffic from Apple.com will flow through fine (ie: websites, Software Update, Apple web services, iCal, etc). This can lead to some problems with other Apple accessed servers though, like .Mac mail, some iChat traffic, and the Network Time Protocol. Of course you can manually edit the IP block list and remove Apple entirely if this is too restrictive for your needs.
If you’re a heavy P2P user, you’d likely benefit from downloading and installing PeerGuardian.
PeerGuardian developer home
Download PeerGuardian for Mac OS X now
PeerGuardian is also available as a free download for Windows and Linux if you’d like to install it on other platforms.
Fix Crashing Apps on Your iPhone and iPad
Nothing is worse than having an app that crashes on you every time you launch it. It can be more frustrating when that app dipped into your wallet before introducing you to the world of app irritation. To help you use your app(s) without throwing your fancy Apple device across the room, follow the steps below. Be sure to check your app after each solution presented below. If your app starts behaving, you can stop and enjoy. If your app is still going all wonky, continue to the next step until it begins working.
Make X11 Gimp Tool Kit (GTK) apps look much more Mac-like
It’s a well know fact that running X11 applications on ae Mac crates a lot of ugliness. There is a way to solve this, at least partially.
A lot of Unix applications use the Gimp Tool Kit, or GTK for short. You can install GTK on Mac via MacPorts by running sudo port install gtk2 in Terminal. There are some themes in MacPorts as well to make your app look like an Air app instead of Win95; they work, but the look is still alien.
However, there is a GTK theme called mac4lin that emulates the Mac look on Linux, but I discovered this can be used on the Mac as well. Download and extract mac4lin and extract and copy one of the archives in the GTK folder to /opt/local/share/themes. Then run gtk-chtheme from MacPorts to change to your new aqua theme. As a final step, click the Font button to set the font to Lucida Grande 10pt, and you’re done.
Remap only the Exposé key for Spaces use on Unibody laptops
The Unibody Macs have some pre-defined function keys that are hard to remap. For those of us who use Spaces, but not Exposé, here’s how to remap the key. The Exposé key on Unibody MacBook Pros can’t easily be remapped through System Preferences without unmapping all the other special function keys, like volume and screen brightness. If you just want to remap the single Exposé key, here’s how to do that:
First, download and install the open source KeyRemap4MacBook System Preferences panel. Once it’s installed, go into System Preferences » Keyboard, and unmap all the special keys by checking 'Use all F1,F2, etc. keys as standard function keys.'
Switch over to the KeyRemap4MacBook panel, and remap all the special keys there, except for the one you want to change (in this case, the Exposé key). Expand the 'Remap F1...F16' section, then click on 'F5, F6 to Functional,' then each of the single key entries for 'F1 to Brightness Down,' 'F2 to Brightness Up,' etc.
Now you’re back to where you’ve started, except you’re allowing the F3 key to fall through to the system. You can go to the Exposé and Spaces panel and make sure F3 isn’t mapped to anything in the Exposé pane, and is mapped to Activate Spaces.